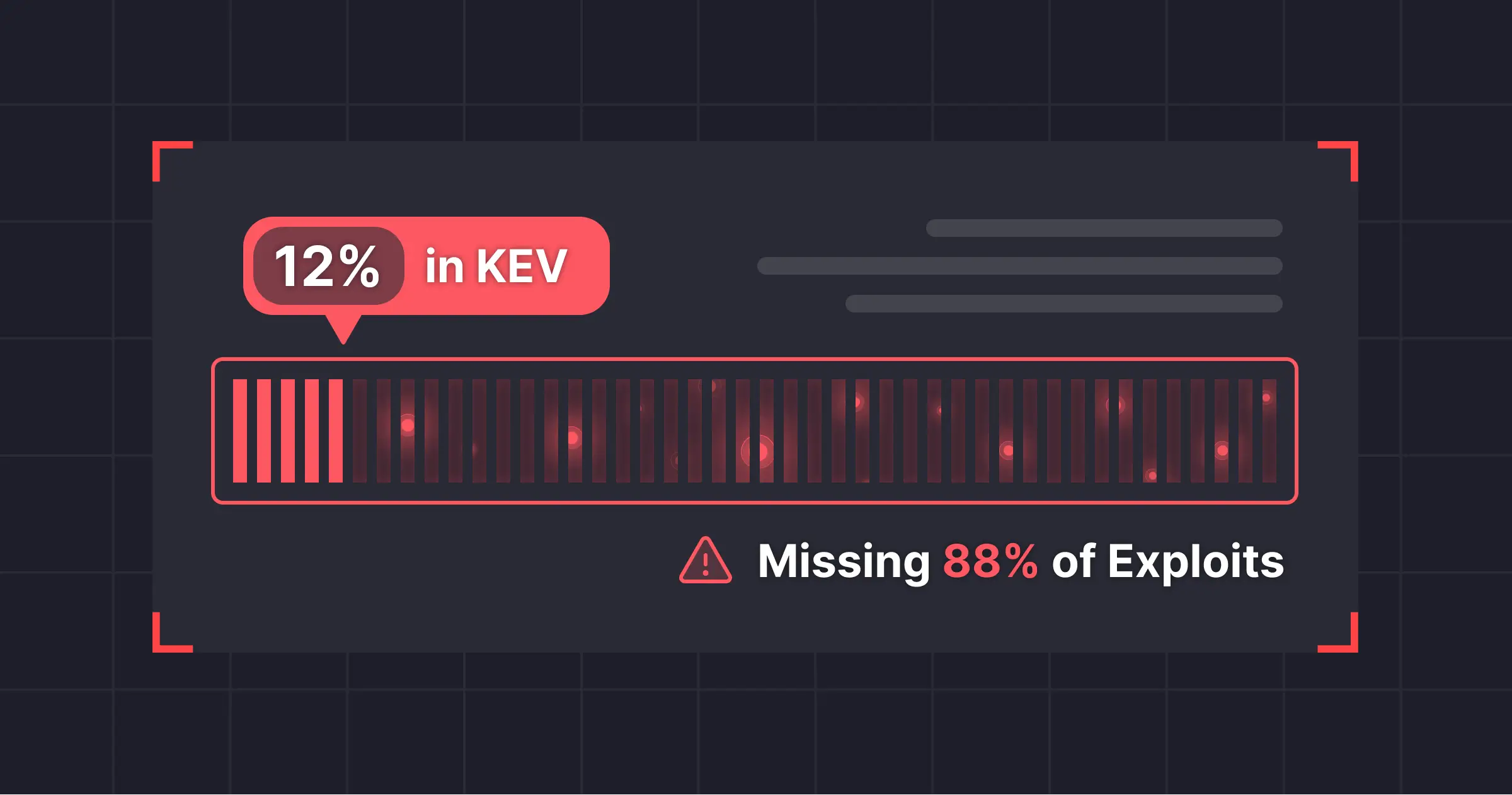
The evolution of application ecosystems within modern organizations has made traditional application security measures inadequate. The rise of microservices, and the complex chains of trust that have emerged are changing what guardrails a team needs in place to meet modern threats with modern application security. It’s time to flip the script on AppSec as we know it today, because the future of comprehensive application security requires ADR.
The Evolution of Application Security
To better understand the need for ADR, it’s important to reflect on how applications have transformed. Just a few years ago, applications were developed by a single, tightly knit team, hosted either on-prem or in the cloud, and shielded by perimeter defenses like firewalls and WAFs. This model worked on several assumptions: that one team understood the entirety of the application, controlled its entire infrastructure, and could deploy static tools to protect it.
However, this approach relied on a series of “ifs” that left critical blind spots. If you knew exactly how your application worked, if every component stayed inside the perimeter, and if there were no third-party services integrated, you had a reasonable chance of defending against attacks. Those days are long gone. In this article, we’ll discuss what’s changed about modern applications, and why security teams need a new breed of tooling to enable effective detection and response.
It’s Time to Take Application Behaviors Seriously
So, why does application security need ADR? The answer lies in essential, real-time, contextual visibility into application behavior. Organizations face the daunting task of understanding how their applications operate internally—across hundreds of microservices, APIs, and third-party integrations. Traditional security measures protect only segments of these applications, leaving blind spots that attackers exploit. These older tools also have isolated contexts - like only seeing processes, network traffic, or the files loaded on a system.
In Miggo’s context, contextual visibility goes beyond surface-level monitoring. It’s not just about seeing how applications behave in real time, but about understanding why those behaviors happen, tracking dependencies, data flows, and business logic. ADR puts suspicious activity into the full context of the application’s operations—tracking API calls, data access patterns, and interactions between components. This level of insight allows security teams to detect deviations early, rather than reacting to isolated alerts that miss the bigger picture.
In today’s landscape, where applications depend on complex chains of trust between microservices, third-party APIs, and integrations, this insight is indispensable. Attackers target these trust gaps, which conventional tools fail to detect. ADR provides visibility into these interactions, enabling organizations to spot vulnerabilities before they are exploited.
Microservices: Increasing the Threat Landscape for Modern Teams
Modern applications are not single, monolithic blocks anymore. They consist of hundreds, sometimes thousands, of microservices—each with its own dependencies and trust relationships. These microservices communicate via APIs, integrate with external vendors, and form chains of trust that extend far beyond the organization’s infrastructure.
But how secure are these chains? Attackers are exploiting the smallest trust gaps, often within the very components you rely on. As applications evolve, so does their attack surface, expanding with each new service or integration. This shift makes conventional security measures inadequate. They lack visibility into these internal interactions and the business logic underpinning them.
Even where monolithic applications still exist, they’re deployed on different architectures than they used to be, creating the same problems. Monoliths still have visibility gaps with traditional tooling, as they now communicate with a variety of cloud native services, fast data caches, and other places where old endpoint tools can’t see. Even monolithic applications are much more connected than ever before.
Traditional Application Security has Inadequate Coverage
Conventional AppSec measures—such as firewalls, intrusion detection systems, and vulnerability scanners—provide static and often limited protection. These tools focus on the perimeter, assuming that threats originate from outside and that applications behave as expected. However, as applications increasingly rely on microservices and third-party integrations, static tools lack the visibility to monitor internal interactions and chains of trust.
With attackers targeting internal trust gaps, traditional AppSec strategies leave blind spots. For instance, firewalls might detect an unauthorized access attempt from an external IP but miss anomalous behavior within a microservice quietly exfiltrating data.
It’s Time to Change the Game with ADR
This is where ADR steps in. ADR goes beyond perimeter defenses by offering real-time, contextual visibility into how applications behave and how their components interact. Instead of waiting for an alert after an attack occurs, ADR enables security teams to detect anomalies early—before vulnerabilities can be exploited.
By monitoring microservice interactions and data flows in real time, ADR uncovers weak points in the application’s chain of trust. It doesn’t just look at static indicators of compromise; it examines how components behave under normal conditions and flags deviations, providing crucial insights into potential breaches.
ADR also helps security teams understand the context of an anomaly. For instance, if a microservice starts communicating with a previously unknown or suspicious service, ADR can alert the team and explain how this behavior could lead to exploitation, enabling rapid, informed action.
The Missing Keys: Proactive Insight and Continuous Monitoring
ADR addresses the gaps left by traditional solutions and enables continuous, real-time monitoring of application behavior at runtime. It’s not just about flagging threats; ADR provides actionable intelligence, helping teams understand how vulnerabilities could be exploited and what business impact they might have.
Instead of only reacting to attacks after they happen, ADR empowers security teams to spot deviations in normal application behavior—whether from unauthorized API calls, suspicious changes in data flow, or unexpected interactions between components. This proactive approach allows organizations to stay ahead of attackers and mitigate risks before they escalate.
Conclusion
As applications become more complex and interconnected, the limitations of traditional security measures become increasingly clear. ADR provides the real-time, contextual visibility necessary to understand application behavior, monitor chains of trust, and detect vulnerabilities before they can be exploited.
For security teams looking to strengthen their defenses in today’s dynamic environment, ADR is not just a helpful tool—it’s essential. By adopting ADR, organizations can enhance their ability to protect applications from evolving, sophisticated threats. Talk to our team to learn more.