Threat Prioritization Based on Runtime Context
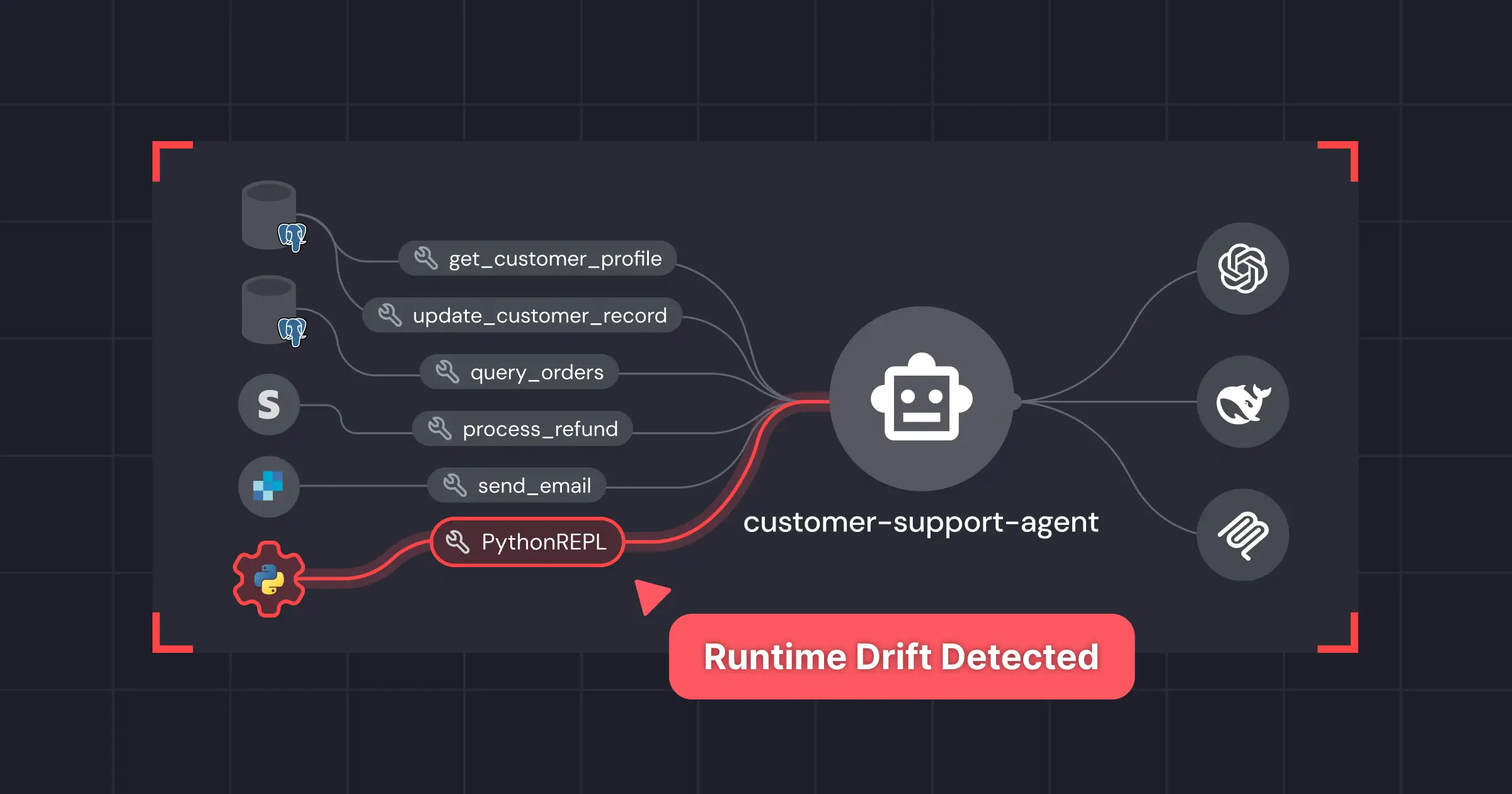
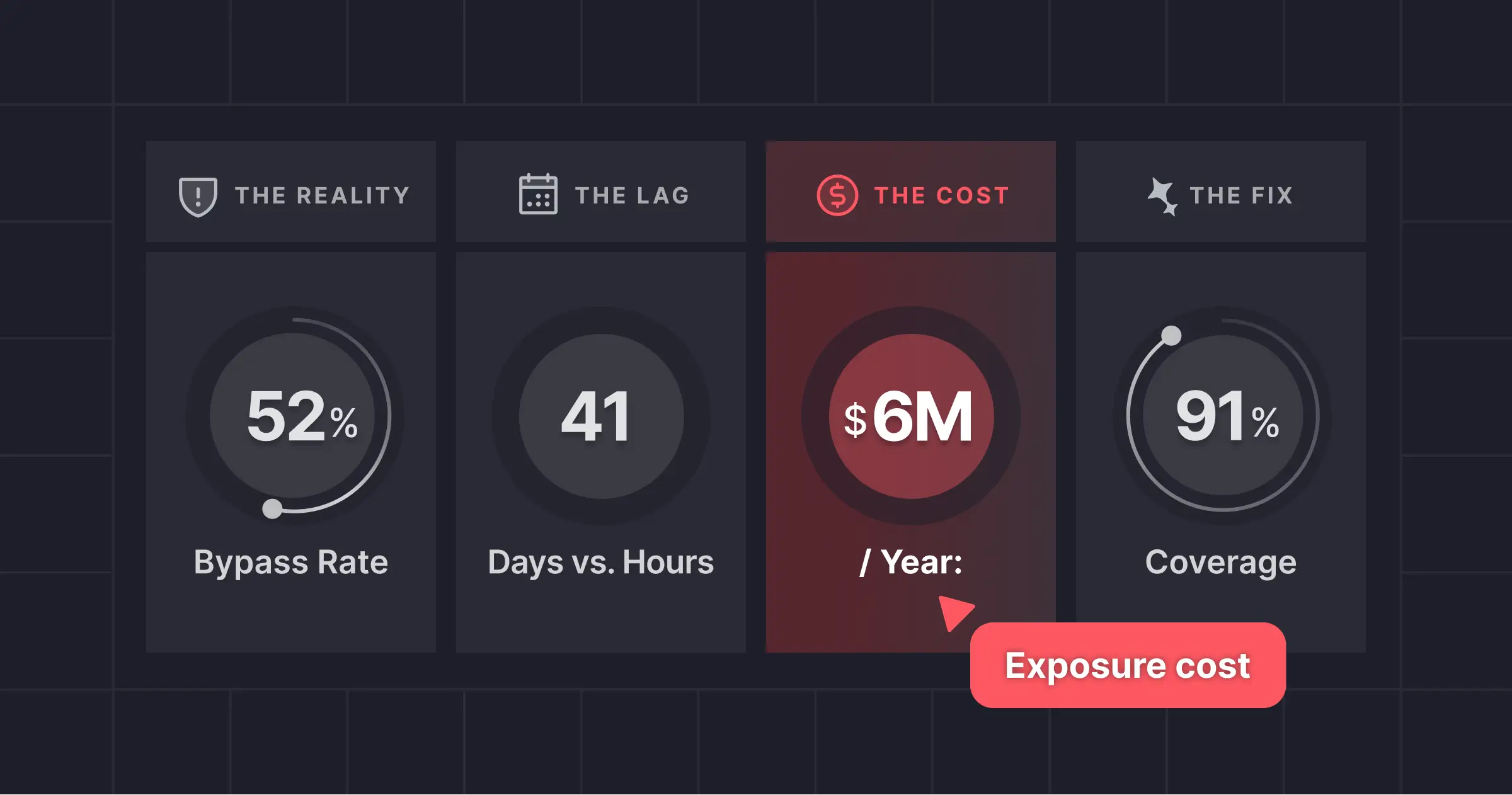
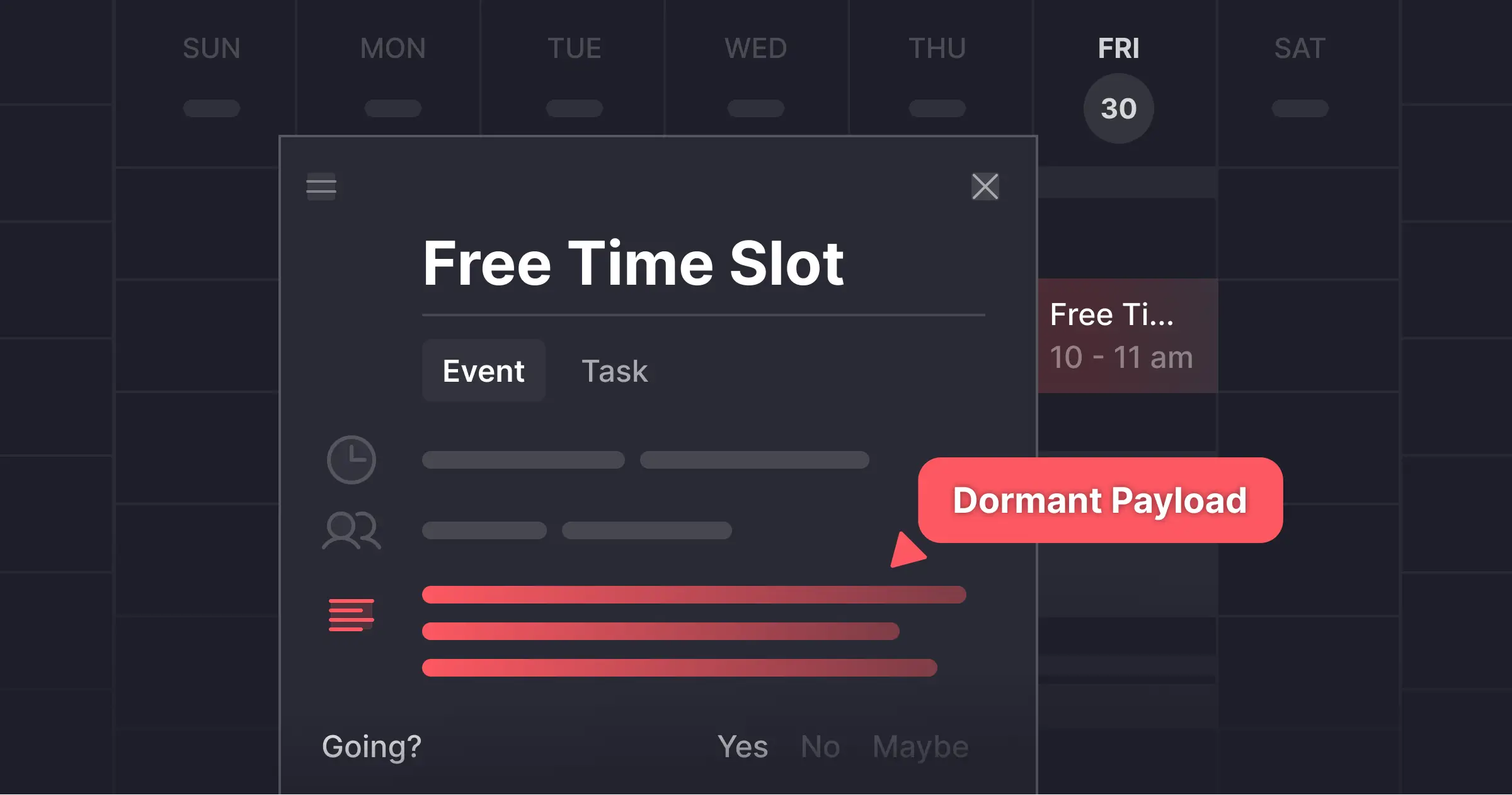
Miggo maintains an accurate and dynamic inventory of all services running within an organization and detects vulnerabilities that are executed and reachable at runtime.
When a new service is added, security teams can review critical insights about that application, including whether it's exposed to the internet or if it has access to sensitive data flows. This enables security teams to focus on what matters most without wasting time sifting through hundreds of false positives.
When a new service is added, security teams can review critical insights about that application, including whether it's exposed to the internet or if it has access to sensitive data flows. This enables security teams to focus on what matters most without wasting time sifting through hundreds of false positives.