TL; DR
Third-party breaches should be managed with the same urgency as any other service compromise within an organization. An immediate impact analysis allows security engineers to assess necessary actions and notify relevant stakeholders promptly. By adopting this proactive approach, organizations can better manage the fallout from third-party breaches and safeguard their operations against potential disruptions.
Third-party service breaches are on the rise as our reliance on outsourced services with inconsistent security measures intensifies. As our attack surface resultingly grows, attackers are able to choose from a wide selection of vectors to gain entry from (Okta breach, MOVEit breach). Over the years, we’ve seen headline after headline reveal the impact these breaches can have on organizations, especially when they involve core application services like Okta’s IdP, MOVEit’s file sharing, Snowflake's data store, Stripe's payments platform or Twilio's messaging services.
Understanding the Breach: The Snowflake Case
Recent incidents, such as those detailed in the Mandiant report, illustrate the nature of attacks targeting Snowflake users. Threat actors, like UNC5537, exploited the availability of compromised customer credentials to gain access to Snowflake environments. Once inside, they exfiltrated sensitive data and leveraged it for extortion by threatening to release the stolen information publicly.
The Role of Snowflake in Organizations
Organizations rely on Snowflake for its robust data warehousing capabilities. Its scalable architecture enables businesses to store, manage and analyze vast amounts of data efficiently and make informed data-driven decisions regardless of data volume or complexity. Large-scale data processing and analytics have become indispensable to organizations aiming to retain a competitive edge in today’s data-driven market, making Snowflake indispensable.
The Pain Points in Handling Third-Party Breaches
Growing reliance on third-parties, while beneficial for rapid development and business goals, also exposes them to significant risks from third-party breaches. This includes services such as payments (Stripe), communications (Twilio), Identity (Auth0), AI (OpenAI), chats (Slack), and CRM (Salesforce) that are integrated within customer and business applications to drive innovation and efficiency. When a breach occurs, organizations are bound to face several pain points:
Lack of Immediate Visibility: Once a third-party breach occurs, organizations often have to wait for breach reports and guidance, leaving them in the dark about the immediate impact on their operations.
Dependency on External Responses: Organizations are dependent on the affected third-party vendor to understand the scope and impact of the breach. This can delay their assessment and response efforts, increasing the risk of further
impact.
Clarifying Impact Assessment: Without a clear understanding of what was compromised, organizations struggle to assess the severity and scope of the breach, making it challenging to implement effective mitigation strategies.
Operational Disruptions: The uncertainty surrounding the breach's impact can disrupt business operations, affecting everything from customer service to internal workflows.
The Need for Instant Breach and Impact Analysis
To address these challenges, organizations need a robust breach and impact analysis report that can provide immediate insights into the repercussions of a third-party breach.
It’s vital that these reports include
Service Identification: Identification of services directly or indirectly related to the affected third-party.
Sensitive Data Handling: Analysis of whether sensitive data is handled or related to transactions with third-party services.
Business Flow Overview: Detailed overview of business flows that store or consume data from the affected service.
This comprehensive report can help organizations to
Assess Impact: Quickly determine what was impacted and the severity of the impact.
Implement Mitigations: Identify the necessary mitigation steps to protect their operations and data.
Maintain Operations: Minimize disruptions by understanding which parts of their operations are affected and how to address them.
Breach and Impact Analysis Report: Miggo in Action
Miggo recently identified that one of its SMB Fintech clients was using Snowflake as an integral part of their core customer application. Upon notifying the client of the recent, ongoing security incident at Snowflake, Miggo promptly provided a comprehensive impact analysis report.
The report included the following critical details
Application Services Interaction: A list of direct and indirect application services that communicate with Snowflake.
Sensitive Data Handling: Identification of the types of sensitive data being managed within the Snowflake environment.
Operational Analysis: Examination of the types of operations performed against the Snowflake database, which, in this instance, were limited to read-only actions.
Transaction Metrics: An overview of the transaction rates involving the Snowflake database.
Ecosystem Role: An assessment of Snowflake's general role within the client's application ecosystem.
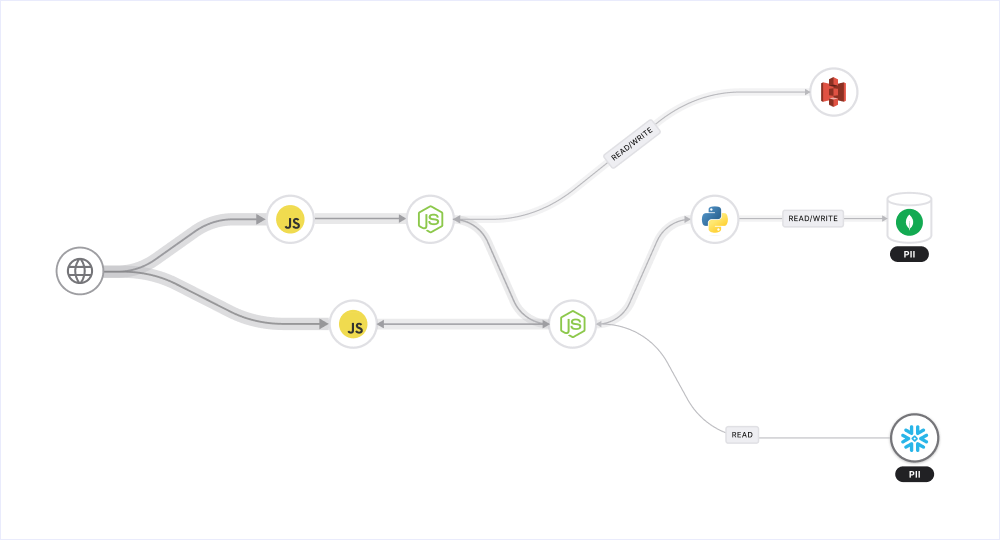
Miggo’s analysis
Impact
Client's minimal usage of Snowflake and the scoped nature of it (Read only access) ensured that the breach had no significant impact on overall business operations or the customer base from the business application perspective.
Outcome
Allowed the client to maintain normal business activities while shifting to a "monitoring mode" for the Snowflake incident.
Additionally, it provided them with the opportunity to enhance their access controls for their Snowflake instance, preparing for potential expanded use in the future and mitigating future similar compromises.
At Miggo, we believe third-party breaches should be managed with the same urgency as any other service compromise within an organization. An immediate impact analysis allows security engineers to assess necessary actions and notify relevant stakeholders promptly. By adopting this proactive approach, organizations can better manage the fallout from third-party breaches and safeguard their operations against potential disruptions.



.png)
