As autumn settles in and the nights grow longer, Spooky Season is a reminder to look beyond the visible and confront what's hidden. The real scares aren't from goblins or ghosts but from unseen integrations quietly embedded into your application infrastructure. This Halloween, it’s time to shine a light on the hidden entities accessing your data without you even knowing.
.webp)
The Challenge of Unmasking Hidden Third Parties
As businesses increasingly depend on third-party services for efficiency and innovation, they often invite unseen entities into their digital domains. Unmasking them is almost impossible, though. Identifying every third-party component woven into a product is like navigating a haunted house with a dingy flashlight—it’s complex, daunting, and fraught with unseen dangers.
Understanding who has access to data isn’t just a compliance checkbox; it’s a critical aspect of an organization’s security posture. Unidentified third parties can become gateways for data breaches, intellectual property theft, and compliance violations, leading to financial losses and repetitional damage.
When Third Parties Come to Haunt Us
Consider the case of a mid-sized enterprise that we’ll call Boo! Inc. They believed they had a solid grasp of their third-party integrations. They have a routine twice-yearly checkup that they write in a nice Google Sheet for their yearly compliance audit. They keep tidy records of what kind of data is shared with each one. Compliance is happy, security is happy, all is a delight!
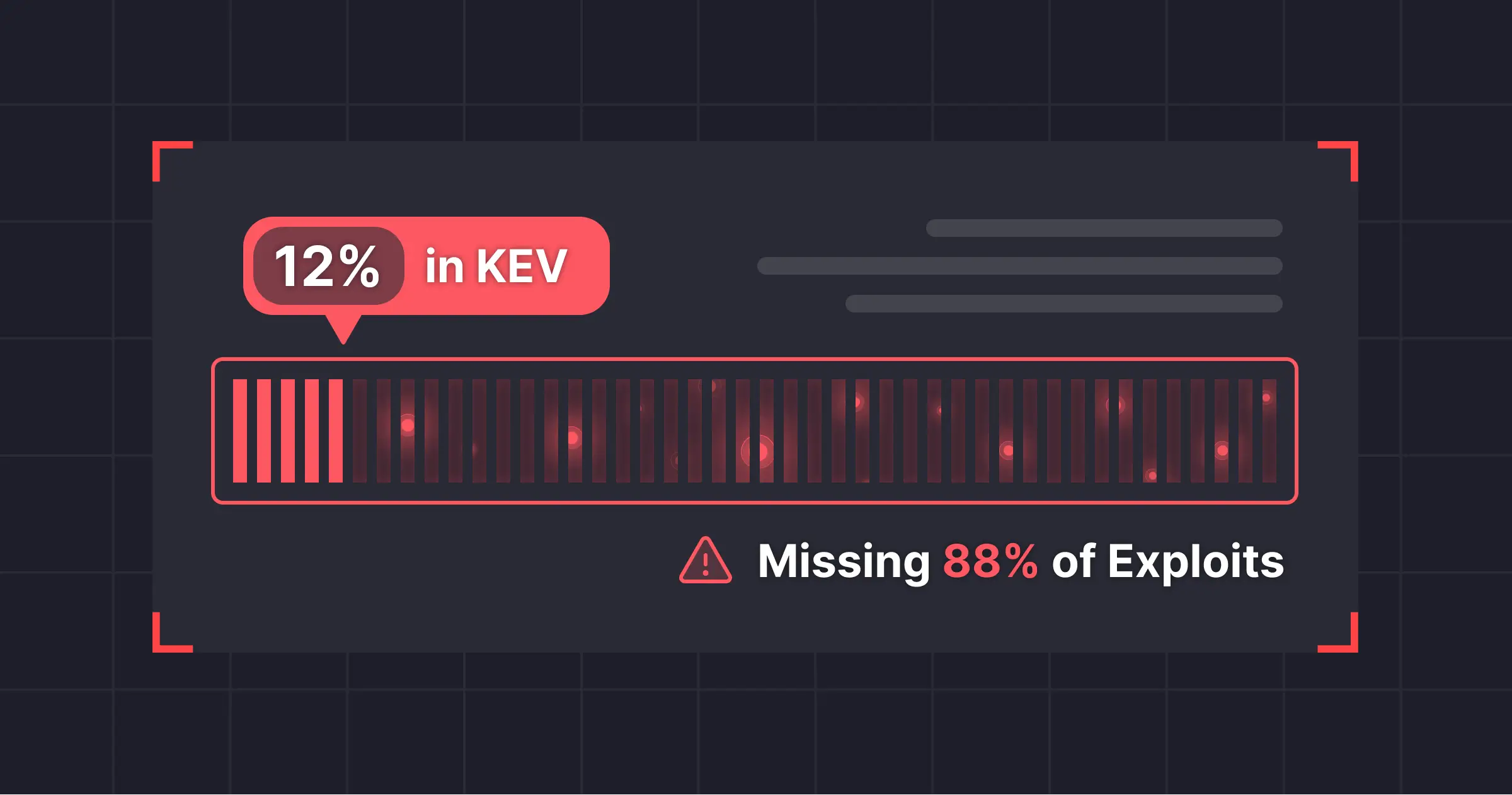
Little did they know that someone signed up to Snowflake's free-tier (without SSO!) and committed a great new product feature to prod. Security? Compliance? What's that?
This critical data point was missed by the entire security department, and they didn't know company data was being stored and shared with a third-party. Not knowing who has access to your data can escalate into a much bigger issue if faced with a breach. So when the 2024 Snowflake breach which exposed 165 customers' data in an extortion campaign happened, Boo! Inc's security team looked at their vendor list and were calm - they didn't even know they used Snowflake.
Imagine your infrastructure being integrated with an AI SaaS, data storage, or any sub-processor without the security team's knowledge. Scary, right? Third party data connections can cause tremendous effects if left unmanaged.
Why Legacy Methods and Tools Fall Short
Most organisations approach third party discovery as they would approach vendor discovery: A compliance issue solved mainly through a process and billing lens. This works for many third parties, SaaS included, but does not take into account the dynamic nature of vendors aimed at software developers. These kinds of issues are more familiar to the security organisation, as they have had to deal with this kind of shift already.
As such, over the past decade or so, several vendors popped up focusing specifically on the SDLC process. This stemmed from license auditing, but was also useful for third parties. These solutions attempt to map out their third-party interactions through manual audits or static code analysis. When done as part of the SDLC or compliance process, they give an organisation a continuous and up-to-date understanding of its third parties, and are good for their original purpose of license auditing. But just like our flashlight, they leave some things to be desired
• Manual Audits: Time-consuming and prone to human error, manual audits can’t keep pace with the dynamic nature of modern applications, missing potential threats that linger in the shadows.
• Static Code Analysis: Limited to examining code without executing it, static analysis overlooks vital, execution-specific behaviors such as dynamic imports and runtime API calls.
Ultimately, these traditional approaches illuminate only what’s directly in front of you, leaving vast areas of your application infrastructure in darkness.
The Need for Runtime Visibility
To truly unmask all third-party interactions, organizations need visibility into the application as it runs in real-time. Runtime application solutions provide critical insight by offering:
•Comprehensive Monitoring: Capturing all external calls and data exchanges during execution, ensuring nothing goes unnoticed.
•Real-Time Alerts: Notifying security teams of unexpected or unauthorized third-party communications.
•Adaptive Learning: Continuously updating the profile of third-party interactions as the application evolves.
By implementing a runtime solution, you equip yourself with a night-vision scope in this haunted house, revealing hidden paths and spooky entities.
Conclusion
While Halloween is proof that we can enjoy scary things, nobody wants to be haunted round-the-clock. Unlike the once-a-year thrill of Halloween, unmasking hidden third parties is a year-round necessity for safeguarding an organization’s data and reputation.Thankfully, new technology is making runtime visibility attainable. A new class of solutions has turned on all the lights to equip security teams with tools needed to reveal and manage every entity that touches company data. At Miggo Security, we’re dedicated to helping you illuminate the shadows within your production environment. Talk to our team to learn how our solutions can provide the visibility and control you need to secure your data against hidden threats.